Vulnerability Assessment and Penetration Testing (VAPT)
Vulnerability Assessment and Penetration Testing (VAPT) are both security services that focus on identifying vulnerabilities in the network, server and system infrastructure. Both the services serves a different purpose and are carried out to achieve different but complimentary goals.
Vulnerability Assessment focuses on internal organizational security, while Penetration Testing focuses on external real-world risk.
What is Vulnerability Assessment (VA)?
A Vulnerability Assessment is a rapid automated review of network devices, servers and systems to identify key vulnerabilities and configuration issues that an attacker may be able to take advantage off. Its generally conducted within the network on internal devices and due to its low footprint can be carried out as often as every day.
Vulnerability Assessment answers the question “What are the issues on my network?”.
What is Penetration Testing (PT or PenTest)?
A Penetration Test is an in-depth expert-driven activity focused on identifying various possible routes an attacker could use to break into the network. In-addition with the vulnerabilities it also identifies the potential damage and further internal compromise an attacker could carry out once they are past the perimeter.
Penetration Testing answers the question “What can a motivated attacker do?”.
What are the deliverables from a Vulnerability Assessment & Penetration Testing (VAPT)?
Ideally a Vulnerability Assessment & Penetration Testing (VAPT) activity should result in the following deliverables:
- Executive Report – A high level overview of the activity conducted, summary of issues identified, risk ratings and action items.
- Technical Report – A detailed report explaining each issue identified, step-by-step POCs for each issue, code and configuration examples to fix the issue and reference links for further details.
- Real-Time Online Dashboard – A online portal that allows team to monitor the audit progress in real time, take immediate actions for high risk issues, track fixes and closure status, etc
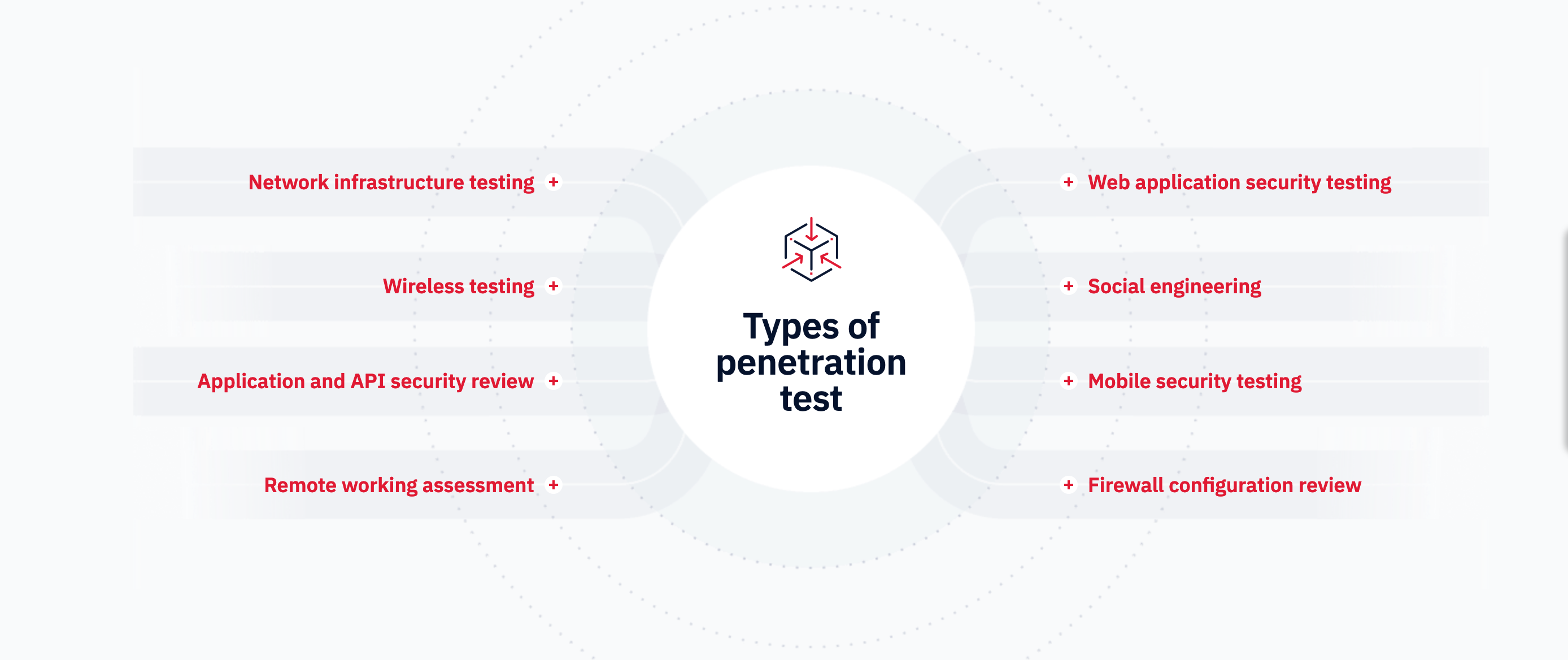
Why Conduct a Vulnerability Assessment & Penetration Testing (VAPT) ?
Cyber attacks and threats are a real-world problem today with thousands of networks and websites and being compromised every day. Some of the normal reasons we see for carrying out a Vulnerability Assessment & Penetration Testing (VAPT) are as follows:
- Customer needs – It is becoming common practice today for customers to request Security Certifications from their partners or vendors.
- Compliance – A large number of industry standards & regulations have included Vulnerability Assessment & Penetration Testing (VAPT) as a mandatory requirement.
- Security validation – Vulnerability Assessment & Penetration Testing (VAPT) helps validate your security controls and measures against real-world attacks.
- Best-practice & data security – As attackers scale and threats evolve, there is a need within organizations to carry out proactive security audits to protect their data and systems from evolving threats.
Compliance standards or certifications for Vulnerability Assessment & Penetration Testing (VAPT)
Vulnerability Assessment & Penetration Testing (VAPT) are largely mandated across various industries and sectors. There are a wide-range of compliance standards that require such audits to be carried out periodically. Some of the well known standards are:
- ISO 27002 / ISO 27001
- PCI DSS – Payment Card Industry Data Security Standard
- SOX – Sarbans-Oxley Act
- HIPAA – Health Insurance Portability and Accountability Act
- TRAI – Telecom Regulatory Authority of India
- DOT – Department of Telecommunication
- CERT-In – Cyber Emergency Response Team of India
- GLBA – The Gramm–Leach–Bliley Act
- FISMA – The Federal Information Security Management Act
- NIST – National Institute of Standards and Technology
- SAS 70 – Statement on Auditing Standards
- COBIT – Control Objectives for Information and Related Technology